VPC Firewall
A firewall is an access control policy that monitors ingress and egress traffic of VPC vRouters and decides whether to allow or block specific traffic based on the associated rule sets and rules.
Concepts
- Firewall rule set: A firewall rule set is a set of rules that a firewall uses
to defend against network attacks. You need to associate a rule set with the egress
or ingress flow direction of VPC vRouter NICs to make the rule set take
effect.
- You can associate a rule set with the egress or ingress flow direction
of VPC vRouter NICs:
- Ingress: applies to the traffic that flows into the specified VPC vRouter via a network.
- Egress: applies to the traffic that flows out of the specified VPC vRouter via a network.
- You can associate a rule set with the egress or ingress flow direction
of VPC vRouter NICs:
- Firewall rule: A firewall rule is an access control entry associated with
the egress or ingress flow direction of VPC vRouter NICs to defend against network
attacks. A firewall rule includes rule priority, match condition, and
behavior.
- You can associate a rule with the egress or ingress flow direction of
VPC vRouter NICs:
- Ingress: applies to the traffic that flows into the specified VPC vRouter via a network.
- Egress: applies to the traffic that flows out of the specified VPC vRouter via a network.
- Firewall rules can be categorized into custom rules and system rules:
- Custom rules: rules that you customize. You can select the
ingress or egress direction that the rules take effect and
configure the rule priorities, match conditions, and
behaviors.
- Rule priority: the priority of a rule to be matched and
take effect when compared with other firewall rules.
Valid values: 1001 to 2999.
- Generally, a rule with a higher priority is primarily matched when compared to a rule with a lower priority. Priorities are represented by using numbers. A smaller number indicates a higher priority.
- Generally, the more specific the match condition that you configure for a rule is, the higher priority you shall configure for the rule.
- Match condition: the condition based on which traffic
flowing into or out of a VPC network is matched. It
includes source IP address, destination IP address,
source port, destination port, packet status, and
protocol.
- You can specify one or more source and destination IP addresses. These IP addresses can be static IP addresses, IP ranges, CIDR blocks, or a mix of the three.
- If you specify multiple entries, which include one or more CIDR blocks, the netmask of the CIDR block must be 24. If you specify only one CIDR block, the netmask of the CIDR block is not limited.
- You can enter a maximum of ten entries, with each entry separated by a comma (,).
- Behavior: the action to be applied to traffic that meets
the match condition. Valid values: accept, drop, and
reject.
- Accept: accepts the traffic that flows in or out of the specified VPC vRouter.
- Drop: drops the traffic that flows in or out of the specified VPC vRouter and does not respond to the client.
- Reject: rejects the traffic that flows in or out of the specified VPC vRouter and responds to the client.
- Rule priority: the priority of a rule to be matched and
take effect when compared with other firewall rules.
Valid values: 1001 to 2999.
- System rules: rules predefined to support system services. The
system predefines the direction that the rules take effect, and
the priority, match condition, and behavior of the rules.
- The priority of system rules ranges from 1 to 1000 or from 4000 to 9999.
- ZStack Cloud has predefined the
following system rules:
- Firewall rules that take effect on the ingress
direction of VPC vRouter NICs:
- Rule 1: The priority is 4000, and the behavior and match condition combination determines to allow established or related data packets from any IP address/port, with any protocol, or to any IP address/port, to flow into the specified VPC vRouter via a network.
- Rule 2: The priority is 9999, and the behavior and match condition combination determines to allow new data packets from any IP address/port, with any protocol, or to any IP address/port, to flow into the specified VPC vRouter via a network.
- Rule 3: the default rule with a priority of 10000. The behavior and match condition combination determines to reject data packets from any IP address/port, with any protocol, in any status, or to any IP address/port, from flowing into the specified VPC vRouter via a network. You can modify the behavior of the rule. Valid values: accept, drop, and reject.
- Firewall rules that take effect on the egress
direction of VPC vRouter NICs:
- Rule 1: the default rule with a priority of 10000. The behavior and match condition combination determines to reject data packets from any IP address/port, with any protocol, in any status, or to any IP address/port, from flowing into the specified VPC vRouter via a network. You can modify the behavior of the rule. Valid values: accept, drop, and reject.
- System rules cannot be modified, except the behavior of the default rule.
- System rules cannot be created or deleted.
- Firewall rules that take effect on the ingress
direction of VPC vRouter NICs:
- Custom rules: rules that you customize. You can select the
ingress or egress direction that the rules take effect and
configure the rule priorities, match conditions, and
behaviors.
- You can associate a rule with the egress or ingress flow direction of
VPC vRouter NICs:
- Rule template: A rule template is a template that you can select when you add rules to a rule set or a firewall.
- IP/Port set: An IP or port set is a set of IP addresses or ports that you can select when you add rules to a rule set or a firewall.
Fundamentals
ZStack Cloud allows you to associate rule sets and rules with the ingress and egress direction of VPC vRouter NICs. Then traffics that flow in or out of the VPC vRouter NICs are filtered based on the rule priority, match condition, behavior, and the effect direction. This ensures the security of data communications across VPC networks, of VPC vRouters, and of user business operations.
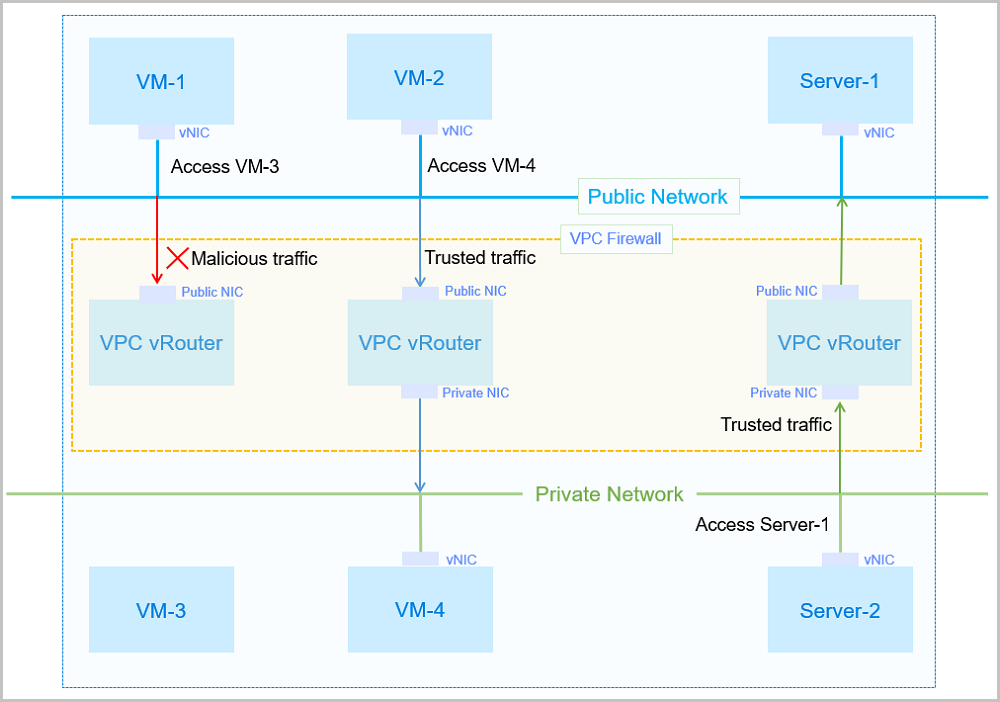
Assume that a server and two VM instances are deployed in a VPC network to run
significant business applications. To ensure business security, firewall rule sets
and rules are associated with the ingress or egress direction of VPC vRouters, so
that only trustful traffics from the public network are allowed to access VM data in
the VPC network and that the server in the VPC network can access the server data in
the public network.
- When VM-1 attempts to access VM-3: The traffic from VM-1 will match the inbound rule set of the public NIC on the VPC vRouter. If malicious traffics are detected, the access is denied.
- When VM-2 attempts to access VM-4: The traffic from VM-2 will match the inbound rule of the public NIC on the VPC vRouter, and then will match the outbound rule set of the private NIC on the VPC vRouter. If trusted traffics are detected, the access is allowed.
- When Server-2 attempts to access Server-1: The traffic from Sever-2 will match the inbound rule set of the private NIC on the VPC vRouter, and then will match the outbound rule set of the public NIC on the VPC vRouter. If trusted traffics are detected, the access is allowed.
Firewall vs Security
A firewall manages the south-north traffic of VPC networks. A security group manages
the east-west traffic of VPC networks and is applied to VM NICs. The two services
complement with each other. The following table compares the two services from three
aspects.
| Item | Security Group | Firewall |
|---|---|---|
| Application scope | VM NIC | The entire VPC network |
| Deployment mode | Distributed | Centralized |
| Deployment location | VM instance | VPC vRouter |
| Configuration policy | Supports only Allow policies | Allows you to customize Accept, Drop, or Reject policies as needed |
| Priority | Takes effect based on the predefined rule sequence | Allows you to customize priorities |
| Match condition | Source IP address, source port, and protocol | Source IP address, source port, destination IP address, destination port, protocol, and packet status |